WHFB Cloud Trust Sign-in On-prem Resource Failure | KDC_UNKOWN_ETYPE 0xc00002fd
In this scenario, Windows Hello for Business and Cloud Trust Policy are configured in Intune. Login using Cloud Trust is successful, but there is a failure when accessing on-prem resources using a PIN code.
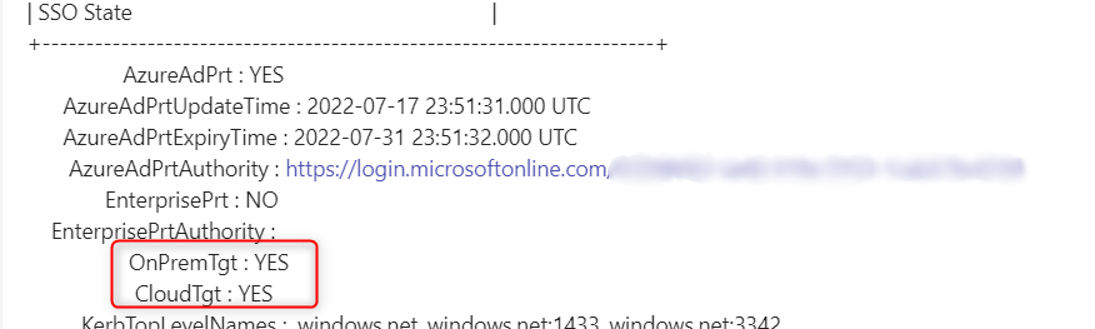
Using “Klist Cloud_debug”, the Cloud TGT appears to be normal.
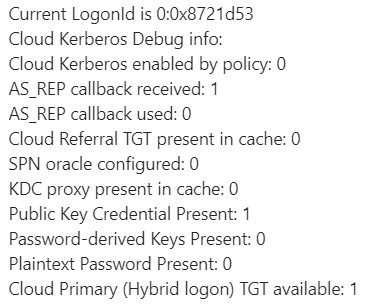
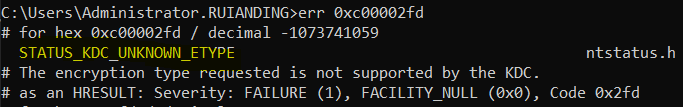
After analyzing the kerberos.etl file in the Authlog package, the following error was found:
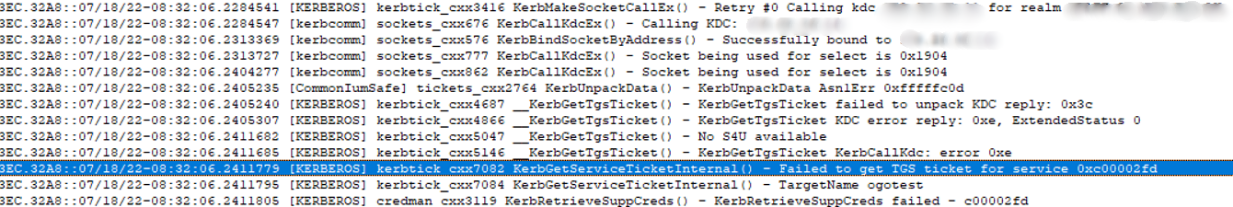
The error indicates a Kerberos Etype error.
After searching extensively, I found in the FIDO2 key documentation (which has similar principles to Cloud Trust) that the AES256 key type must be enabled in order to use it.
According to the documentation, this configuration needs to be set on the Domain Controller. We found a more targeted method with the client: opening “dsa.msc” and enabling the AES256 etype directly under the properties of a specific user.
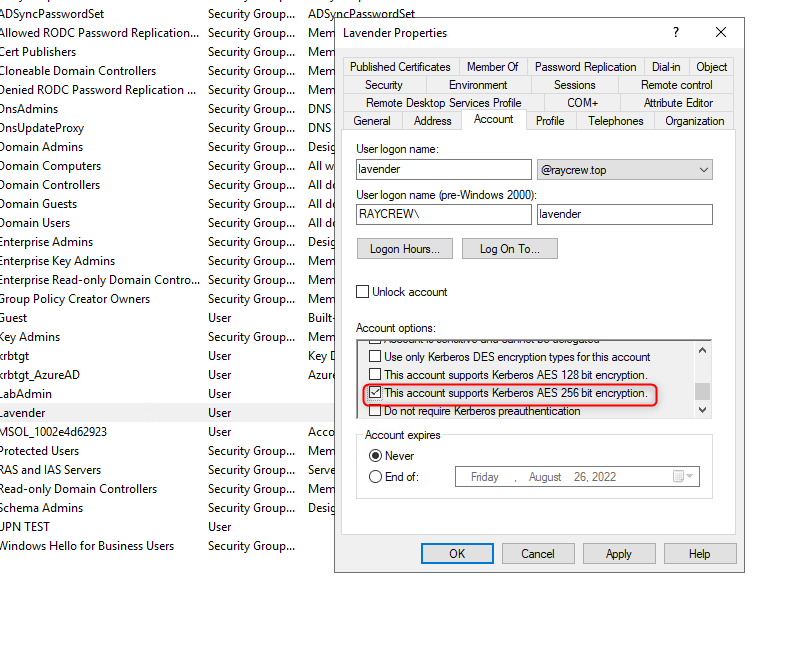
After enabling this setting, we were able to access the mapped drive during testing. Once the AES 256 setting is turned off, access is no longer possible. Therefore, the problem seems to be related to the Etype not being enabled.
Although my own environment continued to function without enabling AES 256, it is possible that the issue is also related to the forest level Etype setting. However, I did not delve deeper into this aspect during this investigation.
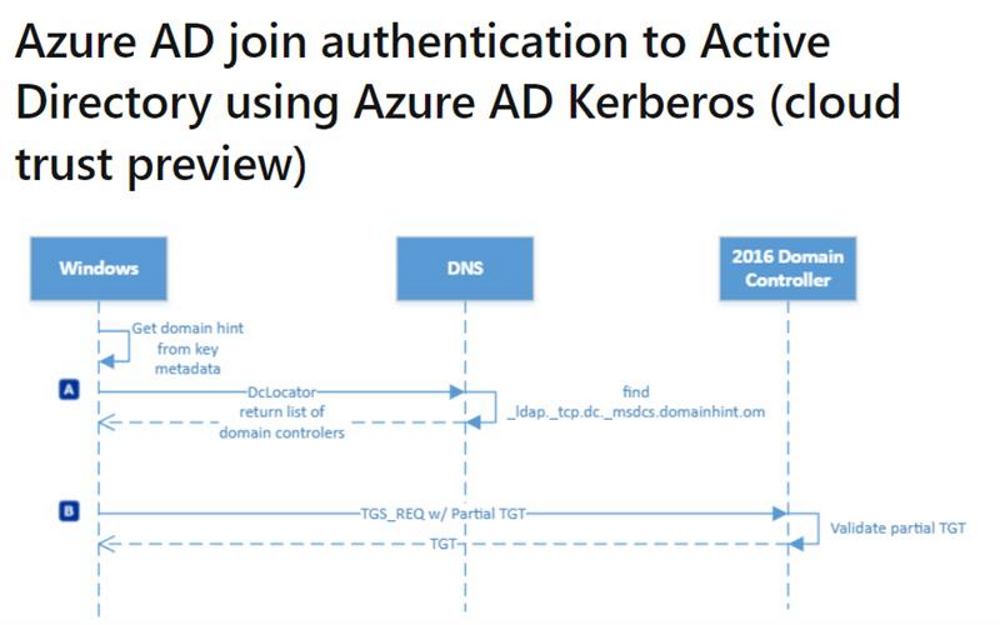
The flow for accessing on-prem resources with Cloud Trust involves using dclocator to locate the Domain Controller and then using Cloud Partial TGT to exchange for an on-prem TGT. This flow is actually simpler compared to key trust and certificate trust.