Testing the ADFS OAuth Flow – Auth Code Grant
Overview
The protocol diagram is showed as below which is very similar to Microsoft identity platform Auth Code Grant flow which involved both authorize and token endpoints:
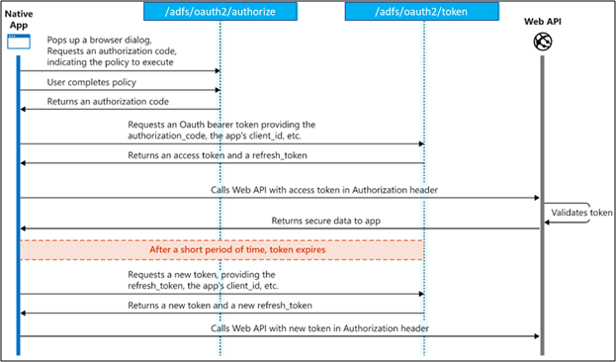
Due to the similarity, we can simply clone the Postman sample in the Microsoft identity platform OAuth flow documentation. And we just need replace some parameters to simulate the OAuth flow in ADFS.
Test in Postman
Firstly, go to this link Microsoft identity platform and OAuth 2.0 authorization code flow – Microsoft identity platform | Microsoft Learn. Find the header Protocol details, later find the Tip and click Run in Postman:
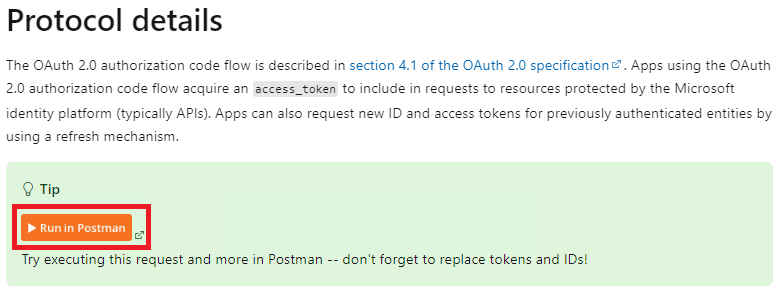
We can either choose clone and run the flow on Postman web or client app. In this demo, I am testing under the Postman native client app.
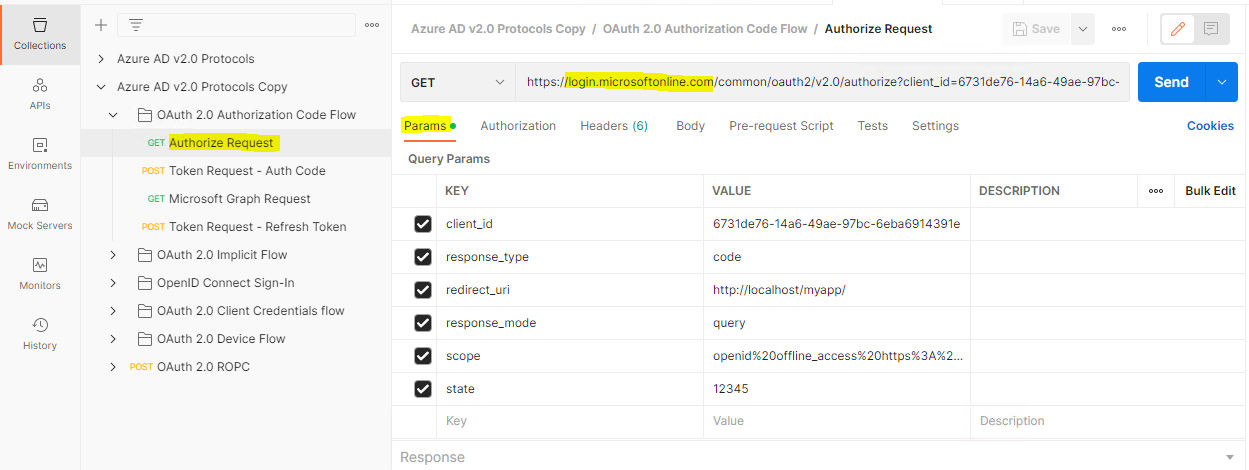
We will see a Collection named “Azure AD v2.0 Protocols” will be created. Expand OAuth 2.0 Authorization Code Flow
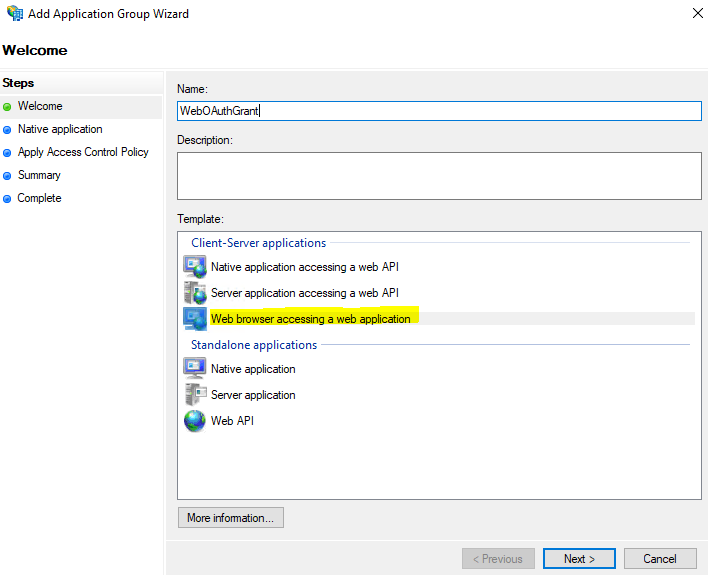
Create the ADFS Application Group
Similar to the OAuth app in Entra ID, we also need to create an app registration entry in our ADFS. Later, we will need to fill out the parameters to obtain the OAuth code.
We will use https://jwt.ms/ as the redirect URI:
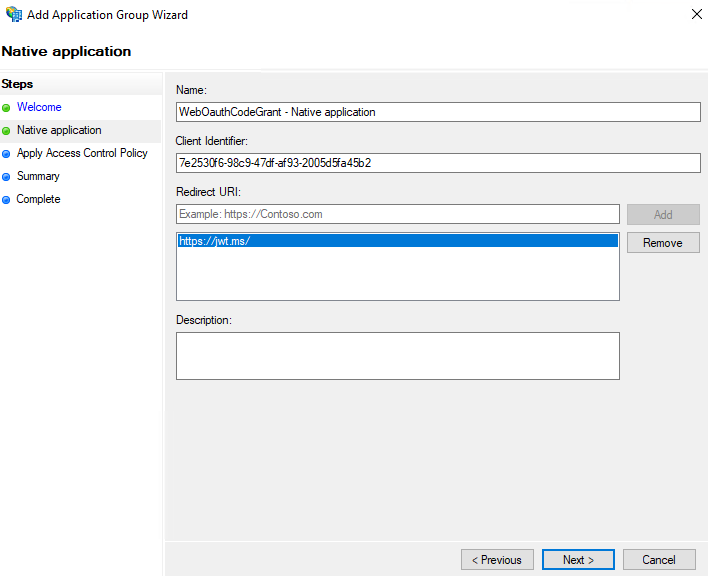
For Access Control Policy, we will choose permit all in this time. Later finish the Add Application Group Wizard
Retrieve the Authorization code
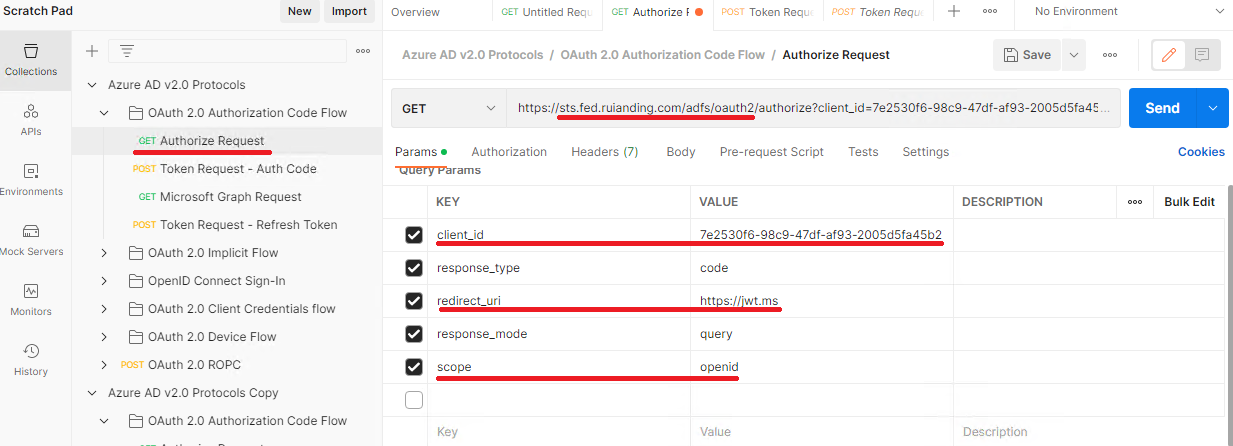
Let’s click the GET Authorize Request, and in this time we will adding some parameters in our HTTP request and sending the request to ADFS authorize endpoint. So make sure the URI has been adjusted as below:https://<yourfedservicedomainname>/adfs/oauth2/authorize
Additionally, please insert the highlighted parameters which can be retrieved from the previous Application Group we’ve created.
Copy the URI and start a new browser windows, throw the URI in the address bar:
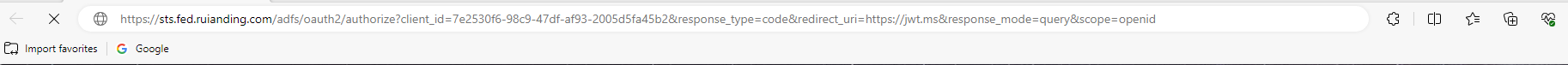
Later, we will be directed to the ADFS login page, and after we finish the ADFS login, we will see the authorization code:
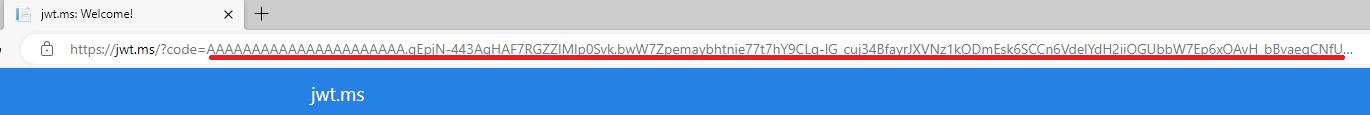
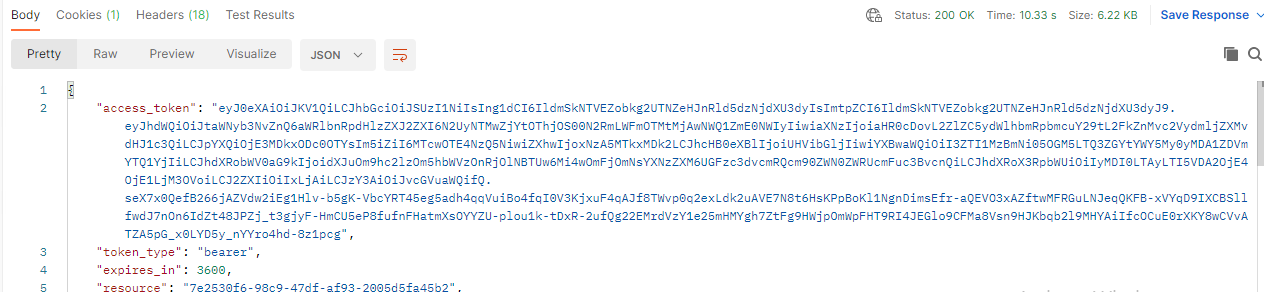
Save the Code and we will use it to get the access token in the next step.
Redeem the Authorization code
Similar to previous step, but as we are using the POST method in this time, we will modify the parameters in the request body:
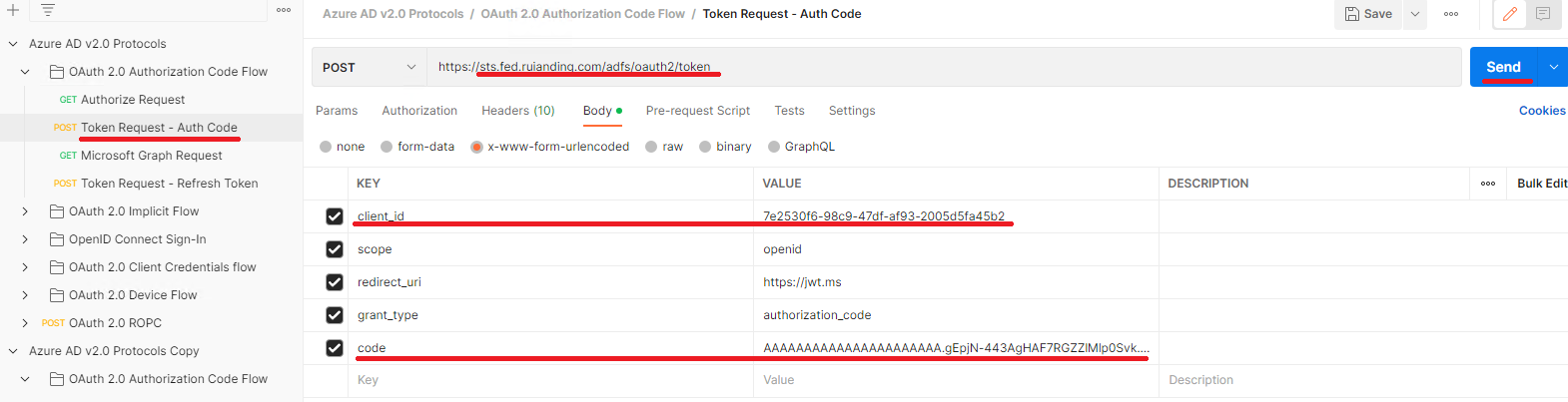
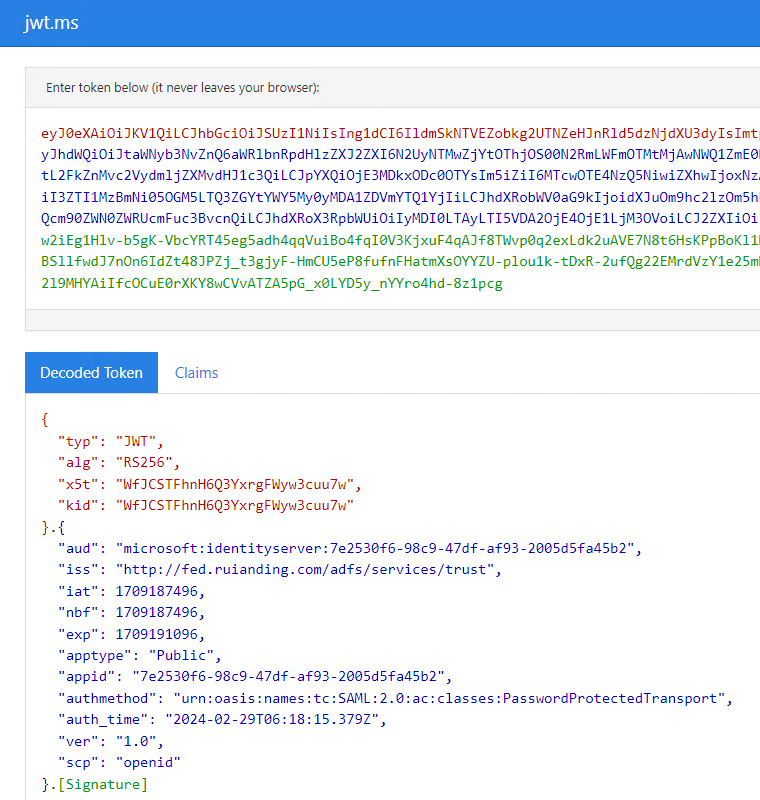
After you click the Send button, we will see the access token returned by our ADFS IdP: