Common DRS Error Codes & Possible Troubleshooting Guides
Overview
After we followed the Configure hybrid Azure Active Directory join guides to set up the hybrid AAD join device, we still might encounter issues that our devices are not able to join Azure AD.
We can always use the command dsregcmd /status to check if the device was joined to Azure AD in the Command Prompt.
For Hybrid Azure AD Joined devices, under Device State:
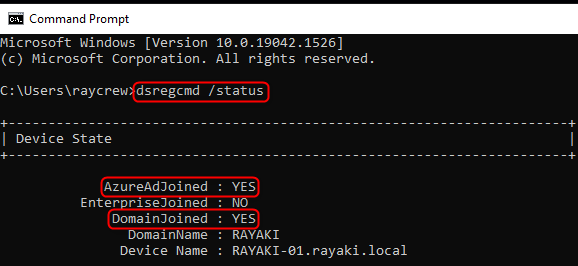
Both AzureAdJoined and DomainJoined value should return YES.
If we did few attempts to Hybrid Join the device but the AzureAdJoined still return NO, we can perform further troubleshooting steps. And in the beginning, let us collect logs from the Event Viewer (eventvwr.msc) > Applications and Services Logs > Microsoft > Windows > User Device Registration > Admin
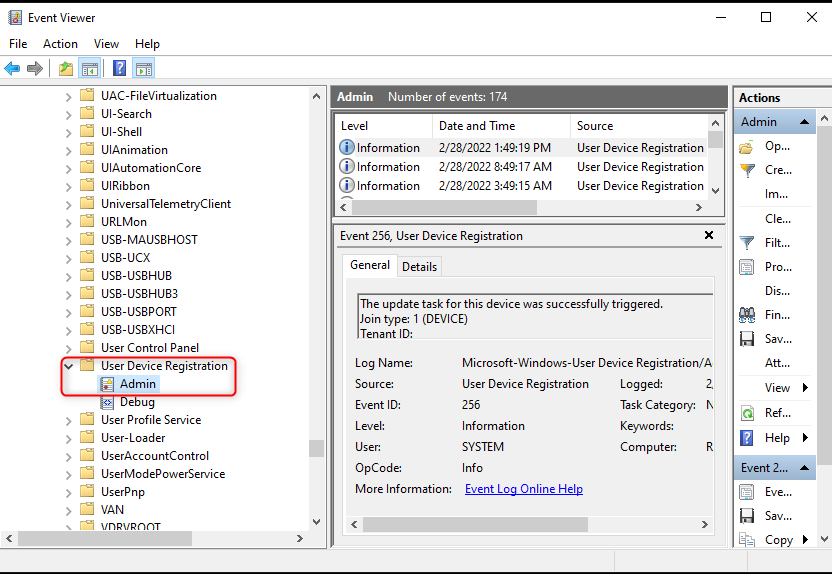
1. Common Errors Codes Combinations and Possible Solutions
User Device Registration – Admin – EventID 304 or 305
AdalResponseCode: 0xcaa1000e
ErrorDescription: The handle is invalid.Recommended step is to check the AD FS claim rules. It is important to have the AD FS claim rules in the described order and if you have multiple verified domains, do not forget remove any existing IssuerID rule that might have been created by Azure AD Connect or other means. Microsoft also recommends using Azure AD Connect wizard to set up device registration. Other way to configure correct claim rules for your Office 365 Relying Party is to use official AD FS claims generator.
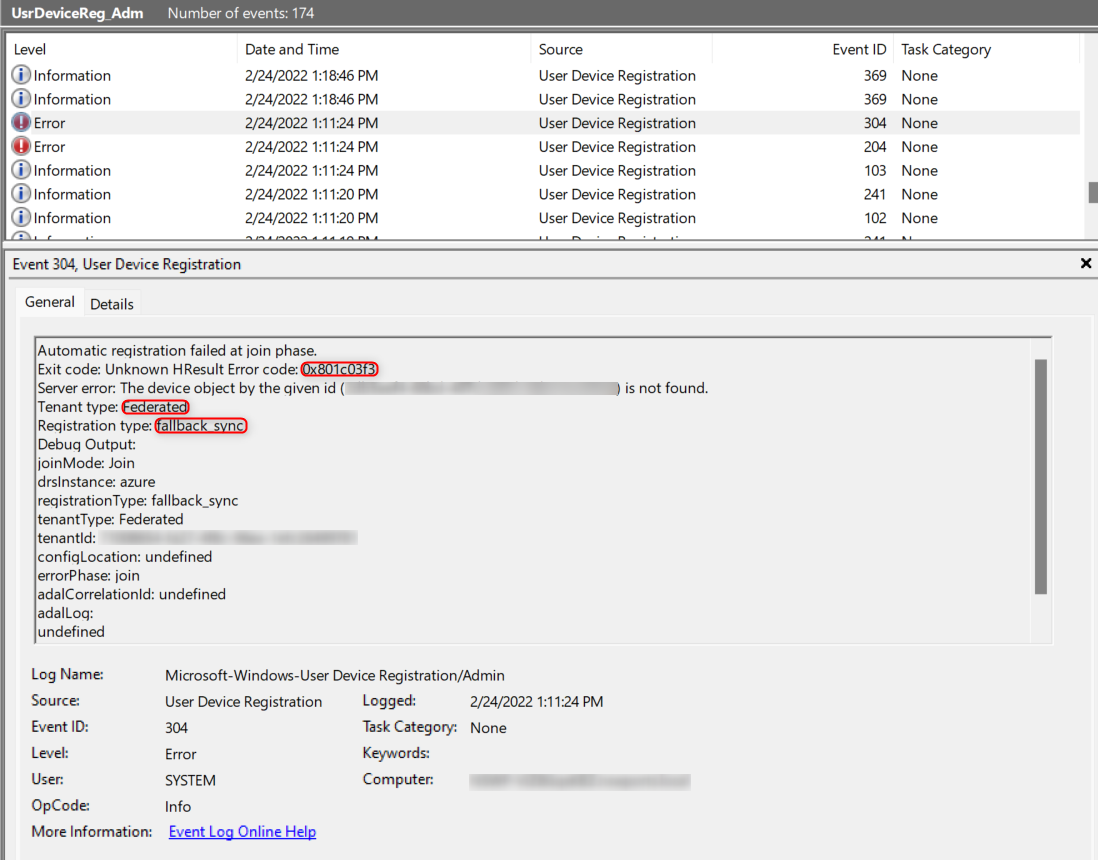
Fallback Sync Join – EventID 304
There could be another senario that thrid party federation services were used, such as Okta, etc. Third party federation services will not support the federated Hybrid Azure AD join, after the federated Hybrid Azure AD join fail it will also return EventID 304 or 305 (Later it will be fallback to sync join, which involves Azure AD Connect and the userCertificate attribute).
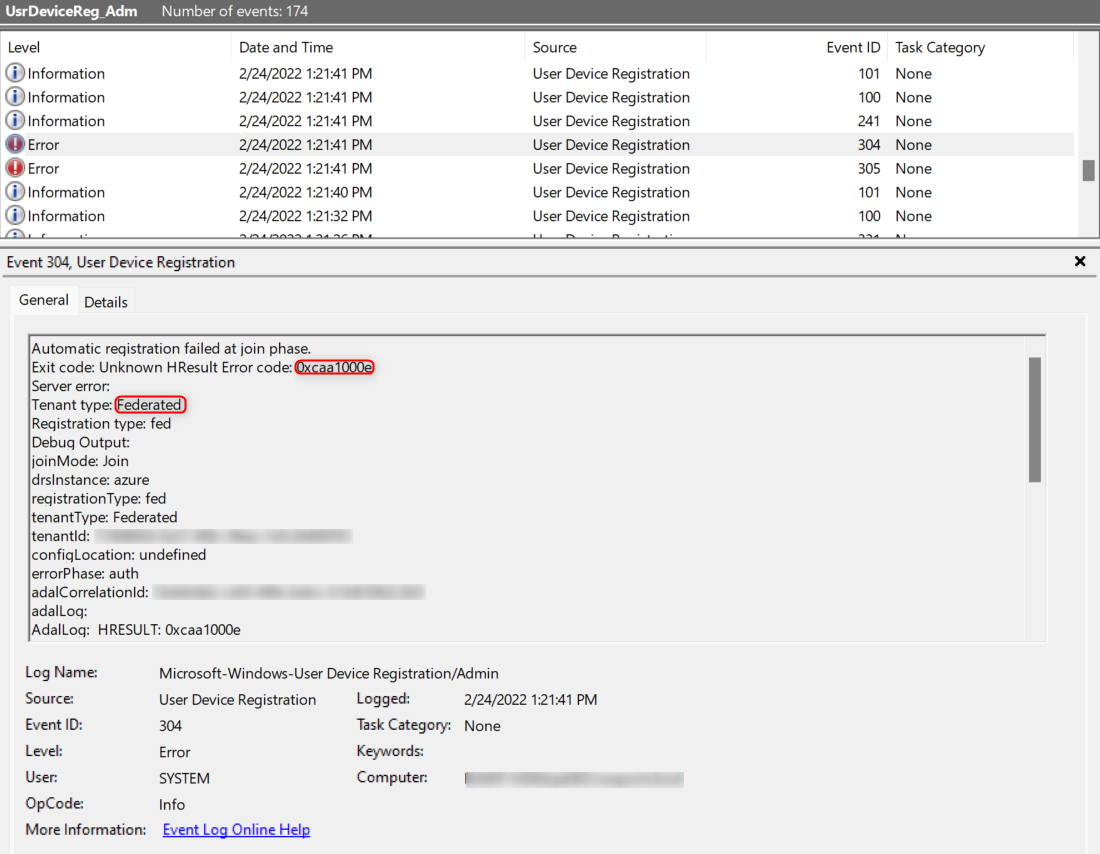
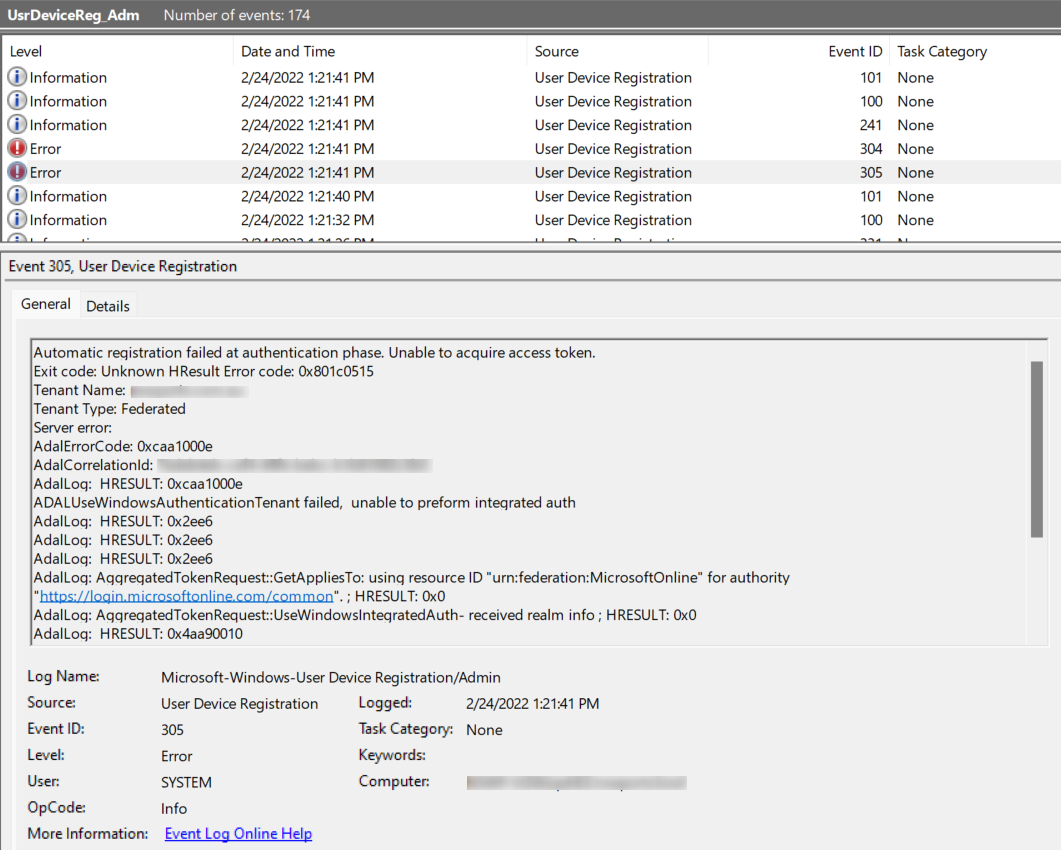
Fallback to Hybrid Azure AD Sync Join
User Device Registration – Admin – EventID 305
AdalErrorCode: 0xcaa90006
ErrorDescription: It failed to get token by WS-Trust flow.Make sure the computer is able to reach and authenticate to specified in the error text description Identity Provider endpoint.
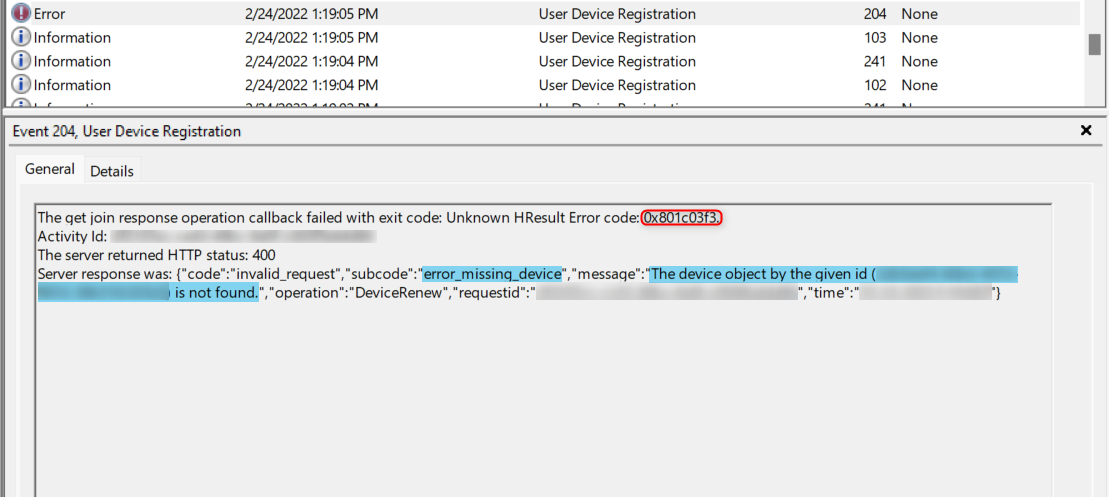
User Device Registration – Admin – EventID 204
ErrorCode: 0x801c03f2 or 0x801c03f3
ErrorDescription: DSREG_E_DIRECTORY_FAILURE or DSREG_E_DEVICE_NOT_FOUND
The device object by the given id (xxx) is not found.
Make sure the on-premises computer object is synchronized to Azure AD. Run the Delta Azure AD Connect Sync PowerShell Command:
Start-ADSyncSyncCycle -PolicyType Delta
User Device Registration – Admin – EventID 204 or 304
ErrorCode: 0x801c03f2
ErrorDescription: The public key user certificate is not found on the device object with id (xxx).Make sure the userCertificate attribute is selected in the Azure AD Connect “Select Attributes” settings of the on-premises connector.
User Device Registration – Admin – EventID 304 (309, 201 and 233 coming before it) or Debug – EventID 500
ErrorCode (Admin Event 304): 0x801c0021
ErrorDescription: DSREG_AUTOJOIN_DISC_FAILED
Errorcode (Admin Event 201): 0x80072efe
ErrorDescription: The connection with the server was terminated abnormally.
ErrorMessage (Debug Event 500): wmain TenantInfi::Discover failed with error code 0x801c0021Most likely the network or proxy didn’t allow the connection to Azure AD device registration endpoints or IdP to complete authentication. See the next error description for the recommended troubleshooting steps.
User Device Registration – Debug – EventID 502
ErrorCode (Admin Event 304): 0x80072ee7
ErrorDescription: The server name or address could not be resolved.
ErrorMessage: WinHttpRequest<class DiscoveryHttpRequest>::OnCallback:The callback handling failed with error code:0x80072ee7Most likely the network or proxy didn’t allow the connection to Azure AD device registration endpoints or IdP to complete authentication. Open a new cmd window as System Account using the psexec tool:
psexec.exe -i -s cmd.exe
You can refer to this post about how to use the psexec tool: Execute Processes Remotely with PsExec Tool
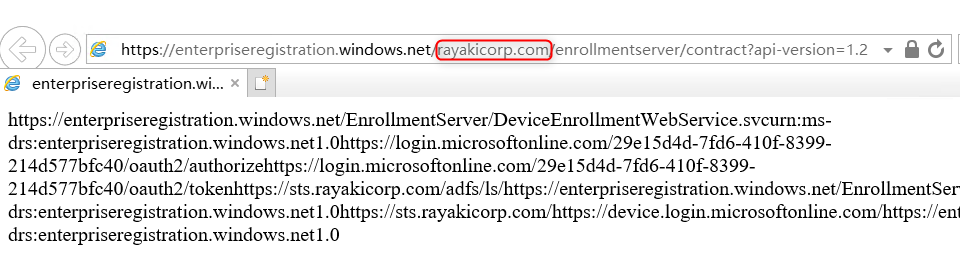
Use the System Account cmd window open a broswer, and try to navigate to:
https://enterpriseregistration.windows.net/<VerifiedDomain>/enrollmentserver/contract?api-version=1.2
Replace <VerifiedDomain> with your own verified domain
You should see the list of device registration service endpoints like this.
If there is a failure, you might want to configure the correct Winhttp proxy settings, and test in the same browser window opened as System Account.
User Device Registration – Admin – 0x80004005
wmain: Unable to retrieve access token 0x80004005
Check the AD FS claim rules.
User Device Registration – Admin – 0xCAA90022
ErrorCode: 0xCAA90022
ErrorDescription: Could not discover endpoint for Integrate Windows Authentication.Check your ADFS settings. It should support Integrate Windows Authentication for WS-Trust 1.3. In case your IdP is not AD FS consult your IdP documentation.
User Device Registration – Admin – 0xCAA9002b
ErrorCode: 0xCAA9002b
ErrorDescription: ADAL – ADALUseWindowsAuthenticationTenant failed, unable to perform integrated auth.
Check your STS settings. It should support Integrate Windows Authentication for WS-Trust 1.3. In case your IdP is not AD FS consult your IdP documentation.
User Device Registration – Admin – 0x801c001d
ErrorCode: 0x801c001d
ErrorDescription: Failed to lookup the registration service information from Active Directory.Check the Service Connection Point settings in on-premises Active Directory.
User Device Registration – Admin – 0x801c0012 or Debug – 0x801c03e9
ErrorCode: 0x801c0012
ErrorDescription: The discovery operation callback failed with exit code: Unknown HResult Error code 0x801c0012. The server returned HTTP status: 400.
ErrorCode: 0x801c03e9The on-premises proxy requiring authentication. Capture network trace while reproducing registration attempt to get more details.
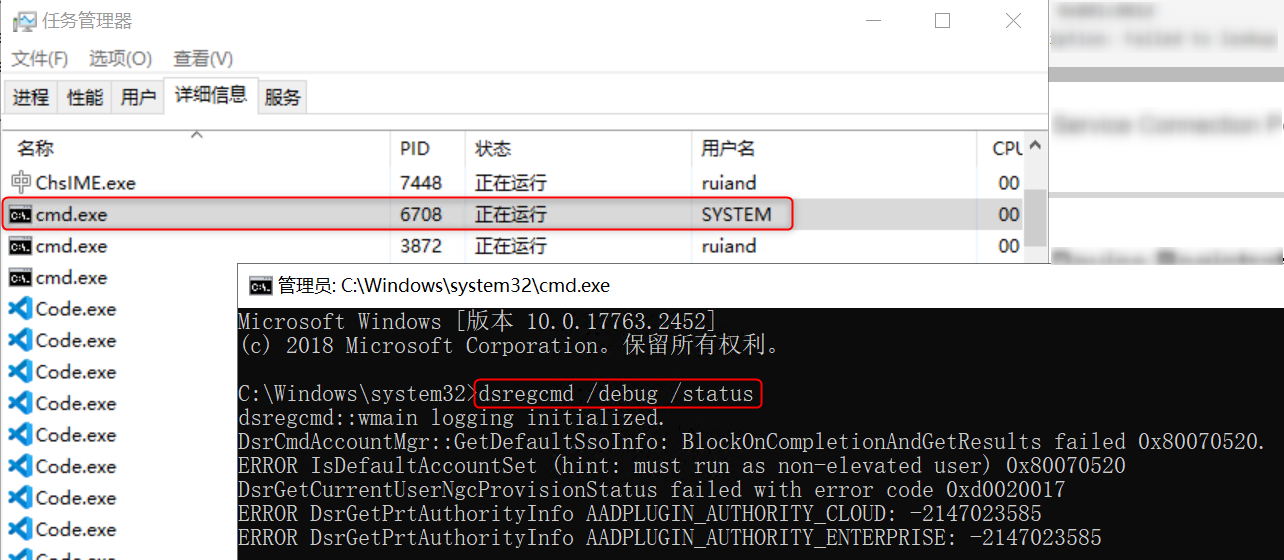
2. Use the Dsregcmd Command with /debug flag to Troubleshoot
dsregcmd /status /debugWe can also use the psexec tool to open a System Account command prompt window to run this command to check if there were errors: